Top 15 Best Security-Centric Linux Distributions of 2019



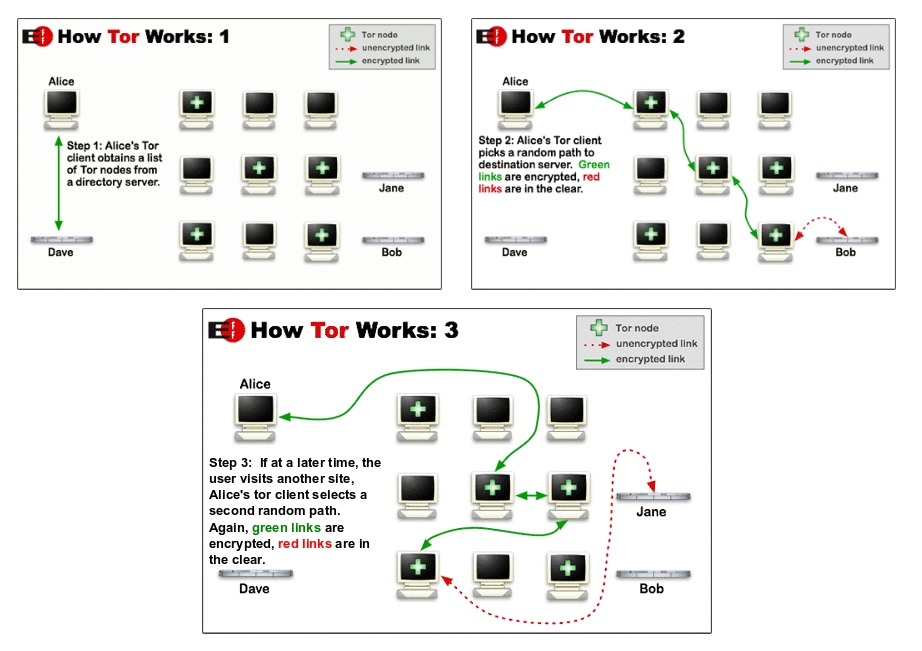
Being anonymous on the Internet is not particularly the same as surging the web safely, however, they both involve keeping oneself and one’s data private and away from the prying eyes of entities that may otherwise take advantage of system vulnerabilities in order to harm targeted parties.
There is also the risk of surveillance from the NSA and several other top-level organizations and this is why it is good that developers have taken it upon themselves to build privacy-dedicated distros that host an aggregate of tools that enable users to achieve both online autonomy and privacy.
In as much as these privacy-centric Linux distros are targetted at a niche in the Linux community, many of them are robust enough to be used for general-purpose computing and many more can be tweaked to support requirements for virtually any specific user base.
A common factor across almost all privacy-centric Linux distros is their relationship with Tor given that many of them come with Tor’s solid anonymity network service built-in and this, in turn, gives users an environment for them to live in safely without any data logs whatsoever, unlike most VPN providers that will still log your real IP address while still being able to see whatever data you may be transmitting at the point of exit of VPN servers.
-

- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 3166 reads
 PDF version
PDF version
More in Tux Machines
- Highlights
- Front Page
- Latest Headlines
- Archive
- Recent comments
- All-Time Popular Stories
- Hot Topics
- New Members
digiKam 7.7.0 is released
After three months of active maintenance and another bug triage, the digiKam team is proud to present version 7.7.0 of its open source digital photo manager. See below the list of most important features coming with this release.
|
Dilution and Misuse of the "Linux" Brand
|
Samsung, Red Hat to Work on Linux Drivers for Future Tech
The metaverse is expected to uproot system design as we know it, and Samsung is one of many hardware vendors re-imagining data center infrastructure in preparation for a parallel 3D world.
Samsung is working on new memory technologies that provide faster bandwidth inside hardware for data to travel between CPUs, storage and other computing resources. The company also announced it was partnering with Red Hat to ensure these technologies have Linux compatibility.
|
today's howtos
|









.svg_.png)
 Content (where original) is available under CC-BY-SA, copyrighted by original author/s.
Content (where original) is available under CC-BY-SA, copyrighted by original author/s.

Recent comments
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago
1 year 11 weeks ago