Server
Canonical and IBM Leftovers
Submitted by Roy Schestowitz on Monday 27th of June 2022 06:15:41 AM Filed under



-
What’s new in Security for Ubuntu 22.04 LTS?
Canonical Ubuntu 22.04 LTS is the latest long term support release of Ubuntu, one of the world’s most popular Linux distributions. As a Long Term Support release, Ubuntu 22.04 LTS will be supported for 10 years, receiving both extended security updates and kernel livepatching via an Ubuntu Advantage subscription (which is free for personal use). This continues the benchmark of Ubuntu LTS releases serving as the most secure foundation on which to both develop and deploy Linux applications and services. In this blog post, we take a look at the various security features and enhancements that have gone into this new release since the Ubuntu 20.04 LTS release. For a more detailed examination of some of these features, be sure to check out the previous articles in this series which cover the improvements delivered across each interim release of Ubuntu in the past 2 years between 20.04 LTS and 22.04 LTS.
-
We Still Want IBM i On The Impending Power E1050
In March last year, as Big Blue was finishing up the development of the Power10 family of Power Systems machines, we wrote an essay explaining that we wanted IBM i to be a first-class operating system citizen on the four-socket Power E1050 machine, which we finally expect to see launch on July 12 if the rumors are correct.
-
Big Blue Tweaks IBM i Pricing Ahead Of Subscription Model
Back in May, Big Blue said that it was going to be simplifying the IBM i stack ahead of a move to subscription pricing for systems software as well as hardware that runs it. To do that means zeroing out prices for a slew of things that had price tags on them formerly.
-
Guru: The Finer Points of Exit Points
Many years ago, we received a call from an IBM i customer stating that all exit points were gone and the QAUDJRN and receivers were missing. Then the question, “Do you think we’ve been hacked?” Truth was, the exit points weren’t gone; the associated programs had been de-registered. Conclusion, they had most likely been compromised.
-
IBM i Licensing, Part 3: Can The Hardware Bundle Be Cheaper Than A Smartphone?
How many monthly iPhone bills is a Power10-based entry server worth?
-
Guild Mortgage Takes The 20-Year Option For Modernization
When Kurt Reheiser returned to the IBM i server after a 15-year hiatus away the platform, things weren’t a lot different than how he left them.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3445 reads
 PDF version
PDF version
Server: InLong and Kubernetes
Submitted by Roy Schestowitz on Wednesday 22nd of June 2022 06:39:33 PM Filed under
-
The Apache Software Foundation Announces Apache InLong as a Top-Level Project
The Apache Software Foundation (ASF), the all-volunteer developers, stewards, and incubators of more than 350 open source projects and initiatives, announced today Apache® InLong™ as a Top-Level Project (TLP).
Apache InLong is a one-stop integration framework for massive data that provides automatic, secure, and reliable data transmission capabilities. The project was originally developed at Tencent in June 2013 and entered the Apache Incubator in November 2019.
-
How to properly adopt and manage Kubernetes in production
Kubernetes is a very important technology in the marketplace because vendors, ISVs, end users and enterprises are all able to come together and use this common infrastructure substrate to build their product on.
In this video for Help Net Security, Alex Jones, Director of Kubernetes Engineering at Canonical, talks about properly adopting and managing Kubernetes in production.
-
Big Data on Kubernetes: The End For Hadoop?
When data sets are too large and/or too complex for traditional software to deal with, we refer to them as ‘big data.’ Organizations and businesses around the world need to use big data to work on projects that influence the way we live now and in the future.
Conversational AI companies want their bots to seem as natural as possible. To achieve this, they must process massive amounts of data in the most efficient and cost-effective way possible. That’s where open source ecosystems like Hadoop come in.
-
Traefik Labs Adds Hub to Simplify Container Networking - Container Journal
Traefik Labs today unveiled a cloud service that leverages agent software to simplify the provisioning of network services for containers.
Manuel Zapf, a product manager for Traefik Labs, says Traefik Hub is a software-as-a-service (SaaS) platform that adds an agent to the open source Traefik Proxy software. That agent makes it possible to instantly authorize access to containers from a single dashboard. That capability eliminates the need to manually configure domain name system (DNS) addresses, routing rules, access control and network access translation to gain access to the internet, he adds.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2278 reads
 PDF version
PDF version
Clown Computing and Red Hat/IBM
Submitted by Roy Schestowitz on Monday 20th of June 2022 01:51:38 PM Filed under

-
Container Threats in the Cloud: What Enterprises Need to Know
-
What you need to know about site reliability engineering
What does that mean? Unlike traditional system administrators, site reliability engineers (SREs) apply solid software engineering principles to their day-to-day work.
-
8 open source Kubernetes security tools | Red Hat Developer
Security remains a top concern for developers working with containers and Kubernetes. In a just-released paper from Red Hat, the 2022 State of Kubernetes security report, 93% of respondents experienced at least one security incident in their Kubernetes environments during the previous year. And 31% of respondents attributed revenue or customer loss to these security incidents.
Innumerable tools exist—including intrusion detection systems, code scanners, and more—to improve security in an increasingly at-risk software development environment. Unfortunately, few of these are built with the unique risks and needs of a Kubernetes environment in mind.
-
Digital transformation: Maximize customer experience in 3 steps
Organizations looking to improve the customer service experience have long turned to digital solutions – to great effect if done correctly. According to McKinsey, organizations that successfully leverage digital products to improve the customer experience are able to increase customer satisfaction by up to 20 percent, reduce the cost to serve by up to 40 percent, and boost conversion rates and growth by 20 percent.
However, to truly impact and improve the customer experience, organizations need to go beyond simply purchasing a product. Research from Boston Consulting Group shows that 70 percent of digital transformation efforts fail, often for reasons that have more to do with implementation than with the actual solutions themselves.
-
Diversity in IT: 3 key components to enable meaningful change
At a recent Tech Titans Industry luncheon, I had the honor of moderating with three distinguished leaders of change on how to improve diversity in IT...
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2567 reads
 PDF version
PDF version
How to Change Default Root Directory of Apache Web Server
Submitted by trendoceangd on Monday 20th of June 2022 08:47:42 AM Filed under
The Apache web server default root directory for storing site content is at the “/var/www/html” path. This directory can be manually changed to the custom directory of your choice.
To achieve this, you need to edit Apache configuration files depending upon the distribution you were using and replace the current directory path with the new location.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2172 reads
 PDF version
PDF version
PostgreSQL 14.4 Released!
Submitted by Roy Schestowitz on Thursday 16th of June 2022 02:53:14 PM Filed under

The PostgreSQL Global Development Group has released PostgreSQL 14.4 to fix an issue that could cause silent data corruption when using the CREATE INDEX CONCURRENTLY or REINDEX CONCURRENTLY commands. Please see the following section for information on how to detect and correct silent data corruption in your indexes.
This release also fixes over 15 bugs since PostgreSQL 14.3 was released in May. For the full list of changes, please review the release notes.
This release is only for PostgreSQL 14. The PostgreSQL Global Development Group will make a scheduled update release on August 11, 2022 for all supported versions of PostgreSQL (10 - 14).
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2076 reads
 PDF version
PDF version
A beginner’s guide to cloud-native open source communities
Submitted by Rianne Schestowitz on Wednesday 15th of June 2022 11:39:48 AM Filed under
Some people think the cloud-native ecosystem has a high barrier to entry. At first glance, that looks like a logical assumption. Some of the technologies used in cloud-native projects are complex and challenging, if you're not familiar with them, so you might think you need proven expertise to get involved.
However, looks can be deceiving. This article provides a detailed roadmap to breaking into the cloud-native ecosystem as an open source contributor. I'll cover the pillars of cloud-native architecture, the Cloud Native Computing Foundation (CNCF), and ways to earn more.
Most importantly, after grounding you in the basics of cloud-native practices and communities, the article provides a three-step guide for getting started.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2097 reads
 PDF version
PDF version
Error resolved: 1698 (28000) Access denied for user ‘root’@’localhost’
Submitted by trendoceangd on Wednesday 15th of June 2022 05:09:10 AM Filed under
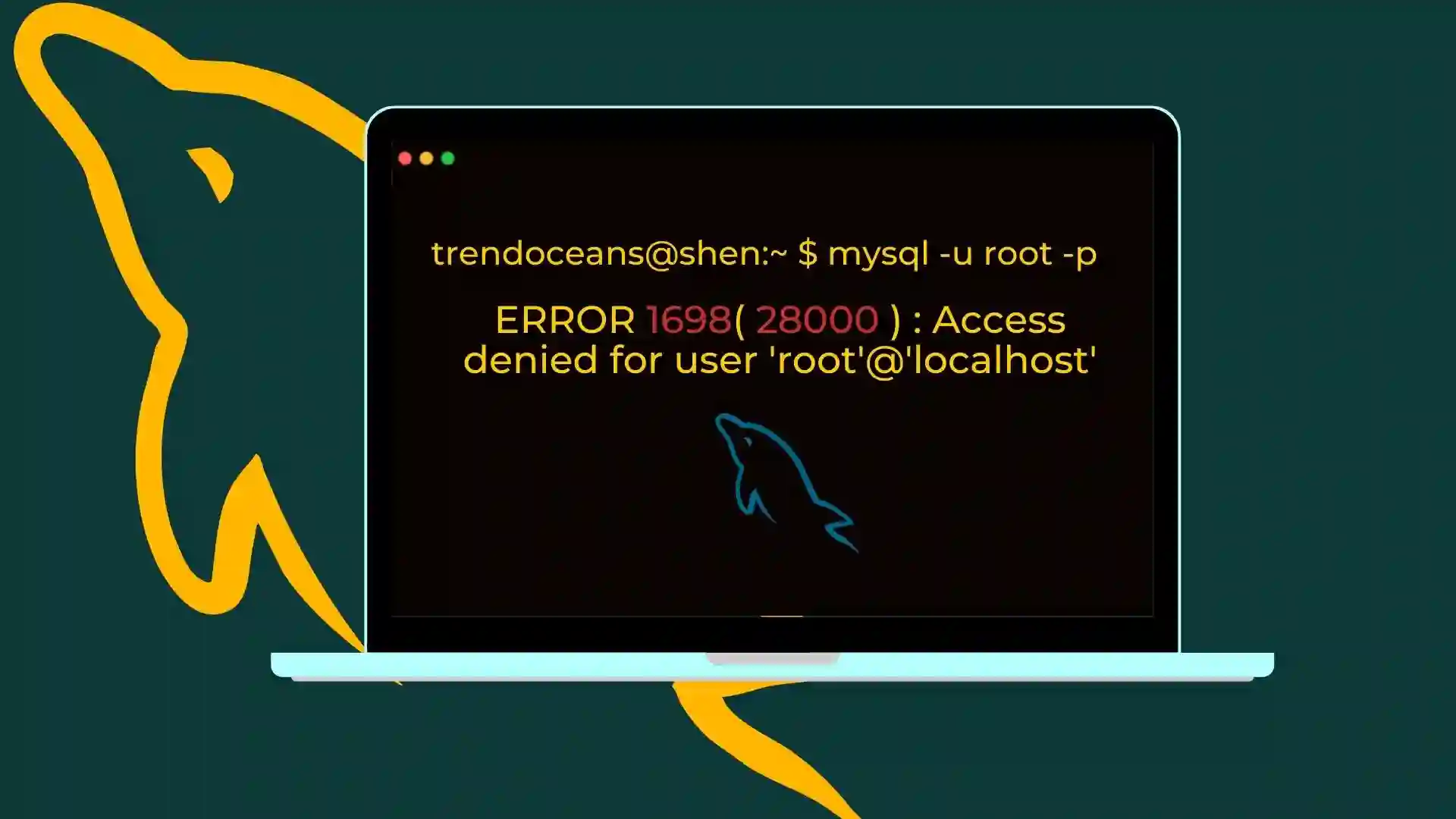
This error is very common when you try to log in to your MySQL for the first time.
Personally, I too faced this issue multiple times, maybe because we were not following the right way to install MySQL, or we forgot to set a password, or else we didn’t get the options to set a password.
Similarly, there may be many other reasons for the above error, but the solution to this error is pretty simple and easy. In this article, you will find a way to resolve 1698 (28000) Access denied for user ‘root’@’localhost’.
There are two ways to resolve this error. First, you will see a simple and less time-consuming method. If the first method didn’t work in your case, then go to the second one.
- 1 comment
 Printer-friendly version
Printer-friendly version- Read more
- 2228 reads
 PDF version
PDF version
EuroLinux 9.0 released
Submitted by Roy Schestowitz on Tuesday 14th of June 2022 03:34:35 PM Filed under


On June 13, 2022, we released version 9.0 of the EuroLinux operating system. It is compatible with the latest upstream release. This release focuses on providing improved default cryptographic policies, a 5.14 kernel, a graphical management interface via a web panel, and improvements related to cloud, virtualization and containerization. "Nine" also introduces a major update in the form of the GNOME 40 desktop environment (with modern GTK 4). An important change for those who want to use EuroLinux on x86_64 architecture, is the need to have a processor supporting x86_64-v2 microarchitecture (also on virtual machines)
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2122 reads
 PDF version
PDF version
Oracle Linux 9 Developer Preview Now Available for Download
Submitted by Roy Schestowitz on Tuesday 14th of June 2022 01:12:48 AM Filed under

We are pleased to announce the availability of the Oracle Linux 9 Developer Preview release for the 64-bit Intel and AMD (x86_64) and 64-bit Arm (aarch64) platforms. Oracle Linux 9 Developer Preview is a major release that introduces many new features, enhancements, and changes. It is 100% application binary compatible with Red Hat Enterprise Linux 9 General Availability (GA) release; Oracle Linux 9 Developer Preview can be leveraged by developers, ISV and IHV to get ready for the GA release of Oracle Linux 9.
Oracle Linux 9 Developer Preview includes security feature updates, networking, high availability, and file system improvements, and enhanced developer tools, compilers, and scripting language support. Oracle Linux 9 Developer Preview ships with the kernel-uek-5.15.0-0.23.1.el9uek Unbreakable Enterprise Kernel 7 (UEK) and kernel-5.14.0-1.7.1.el9 Red Hat Compatible Kernel (RHCK) packages. For details of the new features, enhancements, and changes, refer to the Oracle Linux 9 Developer Preview Release Notes.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2215 reads
 PDF version
PDF version
How to Change Apache HTTP Port in Linux
Submitted by trendoceangd on Monday 13th of June 2022 11:58:52 AM Filed under

In Apache, the default non-secure HTTP connection uses port 80, and the TLS configuration serves the data over port 443.
Today, you will learn how to change the default Apache HTTP port to your custom port in a few steps.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2056 reads
 PDF version
PDF version
More in Tux Machines
- Highlights
- Front Page
- Latest Headlines
- Archive
- Recent comments
- All-Time Popular Stories
- Hot Topics
- New Members
digiKam 7.7.0 is released
After three months of active maintenance and another bug triage, the digiKam team is proud to present version 7.7.0 of its open source digital photo manager. See below the list of most important features coming with this release.
|
Dilution and Misuse of the "Linux" Brand
|
Samsung, Red Hat to Work on Linux Drivers for Future Tech
The metaverse is expected to uproot system design as we know it, and Samsung is one of many hardware vendors re-imagining data center infrastructure in preparation for a parallel 3D world.
Samsung is working on new memory technologies that provide faster bandwidth inside hardware for data to travel between CPUs, storage and other computing resources. The company also announced it was partnering with Red Hat to ensure these technologies have Linux compatibility.
|
today's howtos
|







.svg_.png)
 Content (where original) is available under CC-BY-SA, copyrighted by original author/s.
Content (where original) is available under CC-BY-SA, copyrighted by original author/s.

Recent comments
47 weeks 1 day ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 3 days ago
47 weeks 3 days ago
47 weeks 3 days ago