KDE
digiKam 7.7.0 is released
Submitted by Roy Schestowitz on Monday 27th of June 2022 05:02:30 PM Filed under


After three months of active maintenance and another bug triage, the digiKam team is proud to present version 7.7.0 of its open source digital photo manager. See below the list of most important features coming with this release.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 13392 reads
 PDF version
PDF version
Digitally signing PDF documents in Linux: with hardware token & Okular
Submitted by Roy Schestowitz on Monday 27th of June 2022 12:13:57 PM Filed under


We are living in 2022. And it is now possible to digitally sign a PDF document using libre software. This is a love letter to libre software projects, and also a manual.
For a long time, one of the challenges in using libre software in ‘enterprise’ environments or working with Government documents is that one will eventually be forced to use a proprietary software that isn’t even available for a libre platform like GNU/Linux. A notorious use-case is digitally signing PDF documents.
Recently, Poppler (the free software library for rendering PDF; used by Evince and Okular) and Okular in particular has gained a lot of improvements in displaying digital signature and actually signing a PDF document digitally (see this, this, this, this, this and this). When the main developer Albert asked for feedback on what important functionality would the community like to see incorporated as part this effort; I had asked if it would be possible to use hardware tokens for digital signature. Turns out, poppler uses nss (Network Security Services, a Mozilla project) for managing the certificates, and if the token is enrolled in NSS database, Okular should be able to just use it.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 26453 reads
 PDF version
PDF version
This week in KDE: a mad bugfixing spree
Submitted by Roy Schestowitz on Saturday 25th of June 2022 06:17:56 AM Filed under

Plasma 5.25’s first bugfix release came out a few days ago, and the next one is due early next week. Hopefully most of the bugs you folks found will have been fixed! And among those are few 15-minute bugs too.
Occasionally people ask, “Jeez, it feels like you guys are fixing bugs all the time… shouldn’t they all be fixed by now? Why is your software so buggy?” Thing is, that’s the nature of software. There are always more bugs to fix, no matter how long you work at it. And the more people who use it, the more bugs they’ll find. This is universal, for every piece of software. The best metric is not really “number of bugs fixed,” but rather “egregiousness of bugs fixed.” You want to see that the bugs we fix get weirder and more esoteric over time, which indicates that the basics are becoming more reliable. We’re not all the way there yet, but I believe we are making progress!
- 2 comments
 Printer-friendly version
Printer-friendly version- Read more
- 5436 reads
 PDF version
PDF version
Submit a Goal and Help Shape the Future of KDE
Submitted by Roy Schestowitz on Thursday 23rd of June 2022 11:34:43 AM Filed under

I'm super excited to finally announce the start of the submission process for the brand new KDE Goals!
KDE sets goals that help the community focus on important things that need to get done in collaboration across many teams. Over the years, the community has set goals to tackle issues with usability, made it easier for new contributors to start working on KDE projects, implemented new tech that will serve us for years to come, and much more.
KDE Goals set a direction for the community and help concentrate efforts in areas deemed important by the KDE community itself. Every couple of years, new goals are selected to reflect the communities current priorities.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3663 reads
 PDF version
PDF version
First Beta for Krita 5.1.0 Released
Submitted by Roy Schestowitz on Thursday 23rd of June 2022 09:35:04 AM Filed under


We’re releasing the first beta for Krita 5.1.0 today. Krita 5.1.0 is packed with new features! For the full list, check out the work-in-progress full release notes!
- 1 comment
 Printer-friendly version
Printer-friendly version- Read more
- 4078 reads
 PDF version
PDF version
KDE Plasma 5.25 Desktop Gets First Point Release, Multi-GPU Support Improved
Submitted by Marius Nestor on Tuesday 21st of June 2022 12:18:21 PM Filed under



KDE Plasma 5.25 arrived last week as the latest and greatest version of the beloved desktop environment for GNU/Linux distributions used by thousands of users worldwide.
Now, KDE Plasma 5.25.1 is here as the first maintenance update to KDE Plasma 5.25, addressing various issues like external screen support on multi-GPU setups, an issue with the screen brightness being stuck at 30 percent on some laptops, as well as a KWin crash that occurred when the screen setup changes.
- 3 comments
 Printer-friendly version
Printer-friendly version- Read more
- 3389 reads
 PDF version
PDF version
New KDE Goals: submission stage is now open!
Submitted by Roy Schestowitz on Saturday 18th of June 2022 05:26:48 PM Filed under
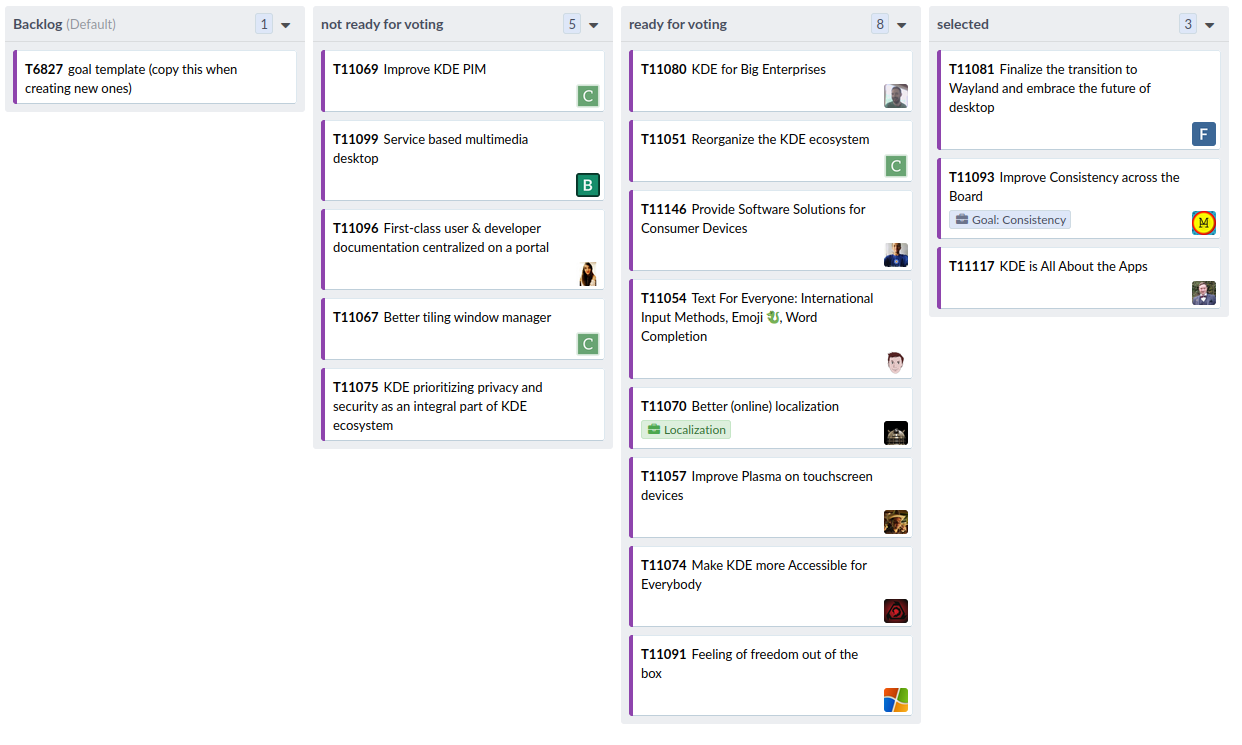
I’m super excited to finally announce the start of the submission process for the brand new KDE Goals!
Starting today, you can submit a new proposal on the workboard and shape the future direction of the KDE community.
This stage in the process lasts 4 weeks, but don’t wait until the last moment! Submit early, and use the remaining time to listen to feedback, refine and update the proposal. Only the submission with good descriptions will move to the next stage: the community vote.
Also: Adding Spaces Horizontal Bar to NeoChat - GSoC'22 post #3
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2905 reads
 PDF version
PDF version
Android Platform Calendar Access
Submitted by Rianne Schestowitz on Saturday 18th of June 2022 07:21:50 AM Filed under

In a previous post about KDE Itinerary I mentioned Android platform calendar support for the KCalendarCore framework. This is meanwhile functional (code), and here are some more details about it.
KCalendarCore not too long ago got a plugin interface for abstracting access to platform calendaring solutions. For this we now have an implementation for the Android platform calendaring API.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2804 reads
 PDF version
PDF version
This week in KDE: non-blurry XWayland apps!
Submitted by Rianne Schestowitz on Saturday 18th of June 2022 07:19:08 AM Filed under
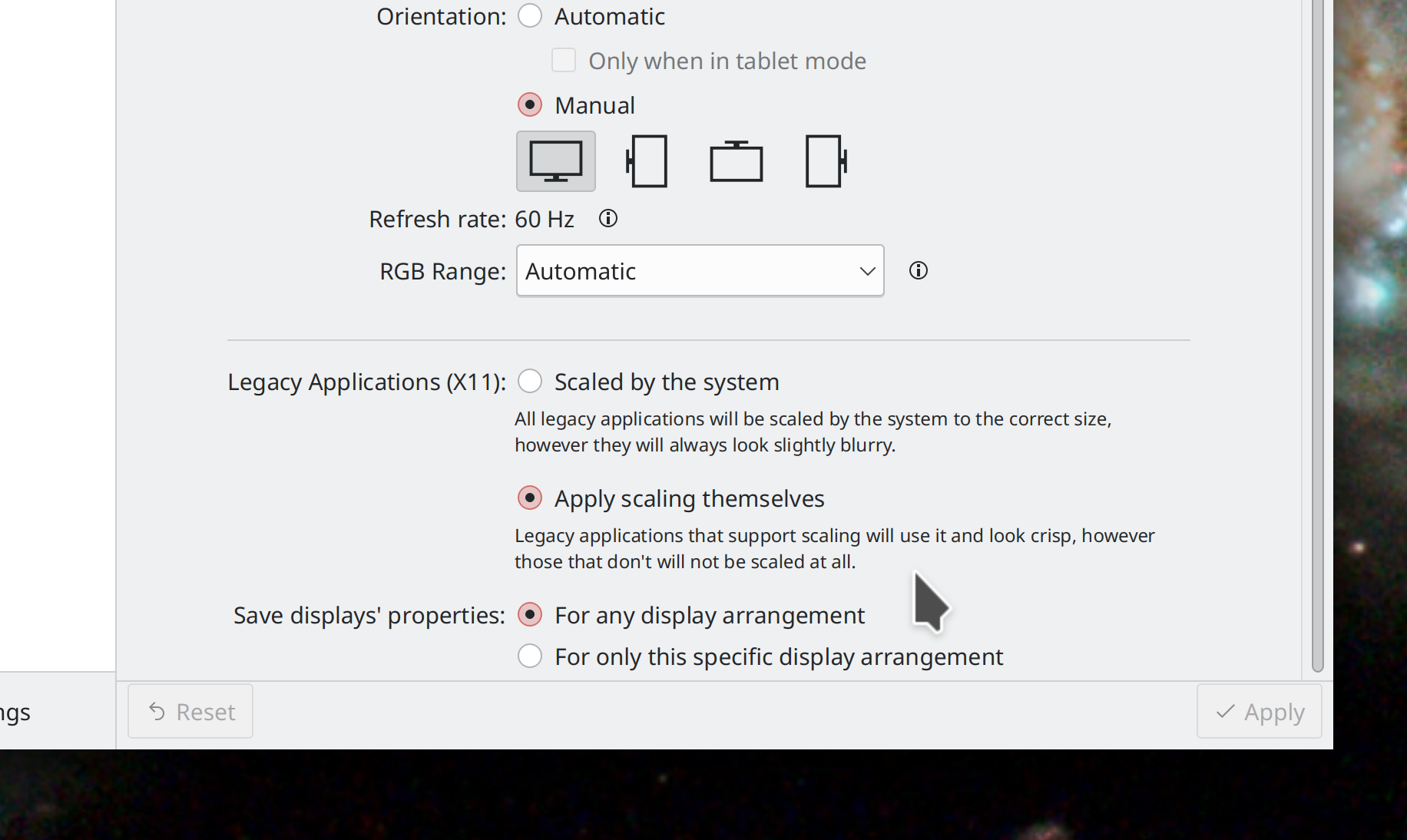
Plasma 5.26 will resolve a major pain point for users of the Wayland session with high DPI screens: you’ll now be able to choose how you want your XWayland-using apps to be scaled:
By the compositor–ensuring uniform scaling, but blurriness (this is the status quo)
By the apps themselves–allowing them to use their pre-existing X11 high DPI capabilities, if they have them, but leaving apps without such capabilities at the wrong scale
So if all the XWayland apps you use support high DPI scaling properly on X11, you can use this new setting to make them look nice and crisp at your chosen scale factor...
- 1 comment
 Printer-friendly version
Printer-friendly version- Read more
- 3023 reads
 PDF version
PDF version
KDE and Kernel Events (Akademy Linux Plumbers Conference, and Kernel and Maintainers Summits)
Submitted by Roy Schestowitz on Wednesday 15th of June 2022 06:00:30 PM Filed under


-
Got something to say about KDE? Say it at Akademy 2022 | KDE.news
Akademy 2022 will be a hybrid event, in Barcelona and online that will be held from Saturday 1st to Friday 7th October. The Call for Participation is still open! Submit your talk ideas and abstracts as the deadline has been extended until the 19th June.
-
Microconferences at Linux Plumbers Conference: Real-time and Scheduling – Linux Plumbers Conference 2022
Linux Plumbers Conference 2022 is pleased to host the Real-time and Scheduling Microconference
The real-time and scheduling micro-conference joins these two intrinsically connected communities to discuss the next steps together.
Over the past decade, many parts of PREEMPT_RT have been included in the official Linux codebase. Examples include real-time mutexes, high-resolution timers, lockdep, ftrace, RCU_PREEMPT, threaded interrupt handlers and more. The number of patches that need integration has been significantly reduced, and the rest is mature enough to make their way into mainline Linux.
-
CFP for the Kernel and Maintainers Summits [LWN.net]
The 2022 Kernel Summit and Maintainers Summit will be held in Dublin; the Kernel Summit will run as part of the Linux Plumbers Conference (September 12-14) while the Maintainers Summit will be on September 15. The call for proposals for both events has been posted. The deadline for the Kernel Summit is tight (June 19), so this is not the time for anybody wanting to speak to procrastinate.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2868 reads
 PDF version
PDF version
More in Tux Machines
- Highlights
- Front Page
- Latest Headlines
- Archive
- Recent comments
- All-Time Popular Stories
- Hot Topics
- New Members
digiKam 7.7.0 is released
After three months of active maintenance and another bug triage, the digiKam team is proud to present version 7.7.0 of its open source digital photo manager. See below the list of most important features coming with this release.
|
Dilution and Misuse of the "Linux" Brand
|
Samsung, Red Hat to Work on Linux Drivers for Future Tech
The metaverse is expected to uproot system design as we know it, and Samsung is one of many hardware vendors re-imagining data center infrastructure in preparation for a parallel 3D world.
Samsung is working on new memory technologies that provide faster bandwidth inside hardware for data to travel between CPUs, storage and other computing resources. The company also announced it was partnering with Red Hat to ensure these technologies have Linux compatibility.
|
today's howtos
|






.svg_.png)
 Content (where original) is available under CC-BY-SA, copyrighted by original author/s.
Content (where original) is available under CC-BY-SA, copyrighted by original author/s.

Recent comments
47 weeks 1 day ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 3 days ago
47 weeks 3 days ago
47 weeks 3 days ago